In vRealize Network Insight 6.6, we introduce a new feature that allows you to focus on your Crown Jewels (Mission critical entities such as VMs or Physical IPs within your multi-cloud infrastructure that require threat protection).
The Crown Jewels can be added and managed within vRealize Network Insight, as shown in Figure 1 below.

Once we have added our Crown Jewels in vRealize Network Insight, we can then run an analysis and define our scope. This will allow you to choose the flow duration included in your analysis and the scope, such as all flows, Entities, or between entities.

After defining the scope, we can proceed with running the analysis, which will give us an overview of any connected entities, reach-ability score, and incoming flows, whether lateral or incoming from the internet.
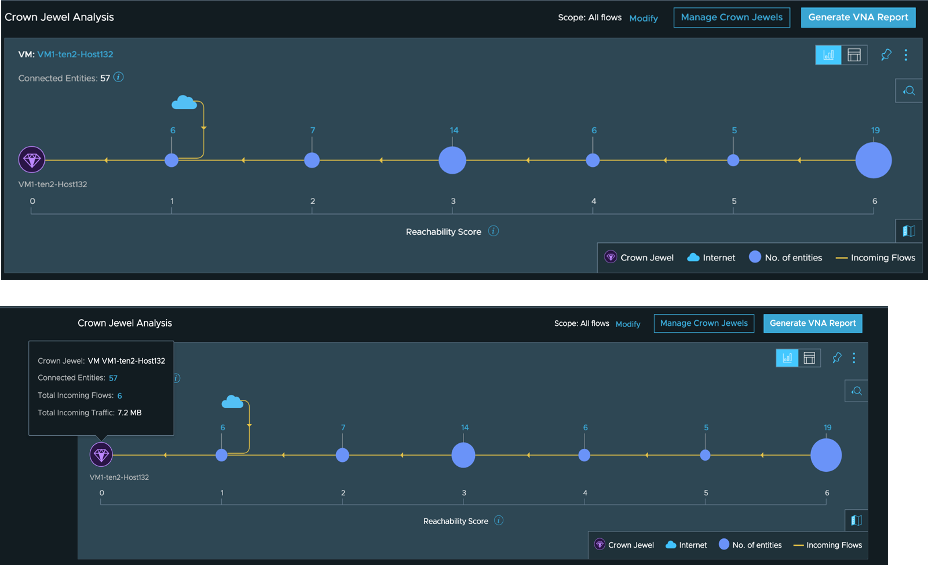
We can also focus on a specific entity to know where it sits in regards to reach-ability, or we can focus on the flows between entities based on the reach-ability score, as sown in Figure 4 below.

Lastly, you will find the option to export the Crown Jewels Analysis report as a PDF document that gives you a list of connected entities and recommended firewall rules to protect your Crown Jewels.

Load Balancers & Applications
It’s become standard practice to deploy a load balancer in front of an application. Whether it is to make the application highly available or restrict and control access to the application via the load balancer. vRealize Network Insight has always had insight into load balancers and applications, but now we’re bringing them together.

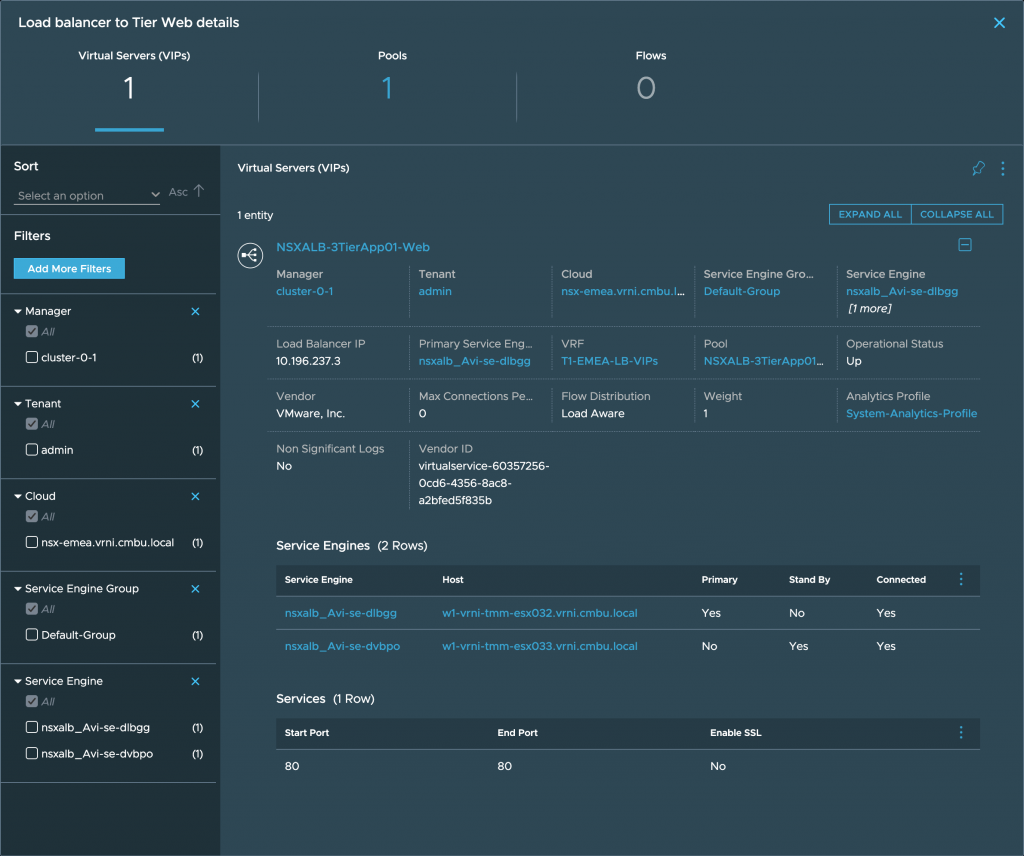
There’s a lot of information on the application dashboard, and customers especially love the real-time application topology diagram. Previously, the application tiers, dependencies on other apps, and the top of rack switches were displayed. Now, any load balancers detected to serve this application are also included.
You can quickly tell which application tiers are served by a load balancer, as there’s a connection to that tier. In Figure 1, you can see the web tier is being served by a load balancer. When you click on the connection to a tier, you get the full details of how that load balancer is configured and its operational status.
Bulk Editing Data Sources
Ever wanted to update the credentials of multiple data sources? Or temporarily disable collections on a group of data sources? Well, with the new data source bulk edit feature, you can! You can now update credentials for multiple data sources at once, disable and enable them, change the polling interval, and change their notes field.
If you’d like to take a quick (2min) look at how bulk updating credentials looks, take a look at the click-through demo below: VIEW
VIEW
Network Assurance and Verification Updates
Cisco UCS, FEX, and NSX-T Bare Metal Edges
Another great new feature in vRealize Network Insight 6.6 is support for Cisco UCS and Cisco FEX in the Assurance and Verification Network Map. This brings excellent visibility into your UCS infrastructure, including all Layer 2 and Layer 3 paths and connectivity. In figure 8 below, you can see the detailed mapping that includes the UCS Blades in the 5108 Chassis, along with the connectivity of each blade to the FEXs and on to the Fabric Interconnects.
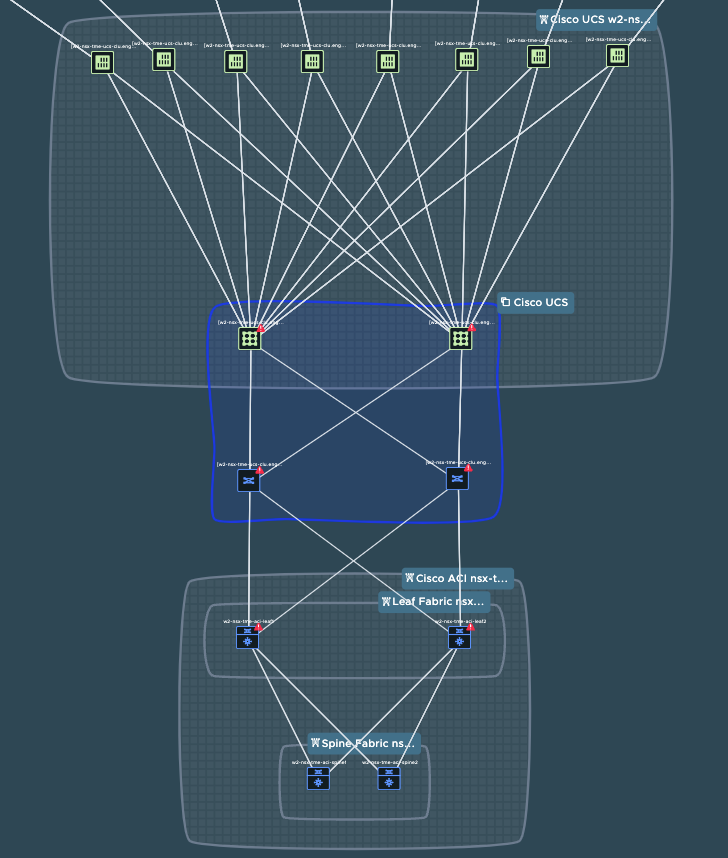
The addition of Cisco UCS and Cisco FEX also enable the capabilities to map paths from device to device or VM to VM.
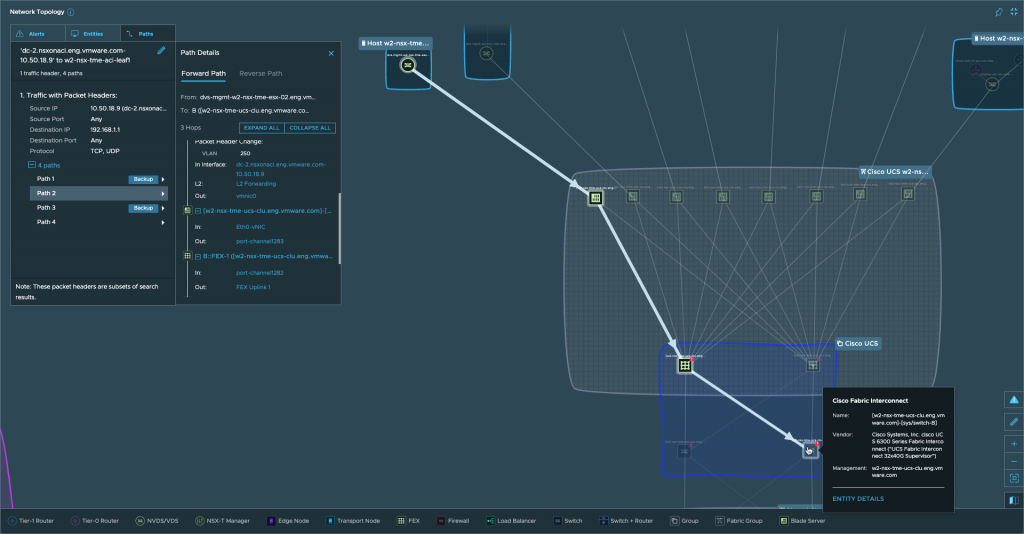
Speaking of Assurance and Verification and the network map, you will also find added support for NSX Bare Metal Edges. Below you will see an example where I have mapped connectivity between the Bare Metal Edge and the TOR Switch to see all possible paths traffic can take along with blocked paths.
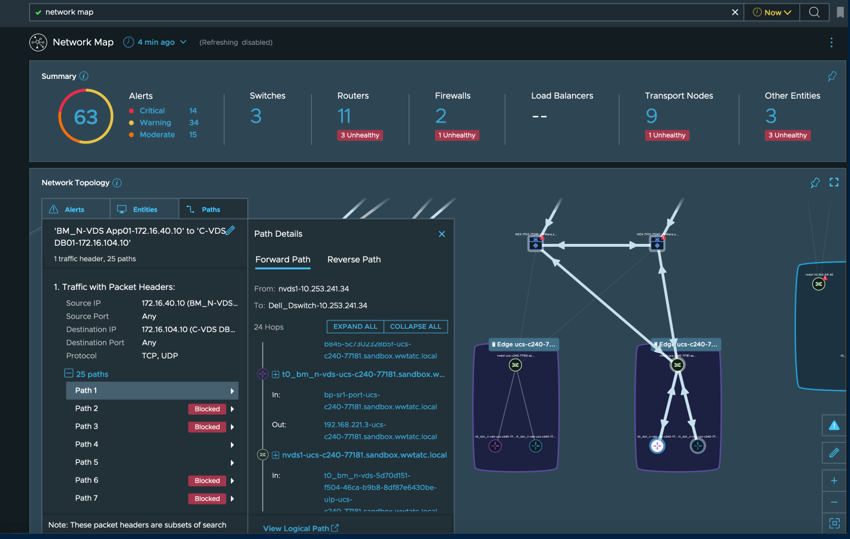
Figure 10. Path Mappings from NSX Bare Metal Edge to TOR Switch