Using private endpoints, Azure Private Link enables you to securely connect Azure PaaS services to your virtual network. You only need to set up one endpoint per resource for several services. As a result, you may use Azure Arc to connect your on-premises or multi-cloud servers and send all traffic through a site-to-site VPN connection or Azure ExpressRoute connection as opposed to using open networks.
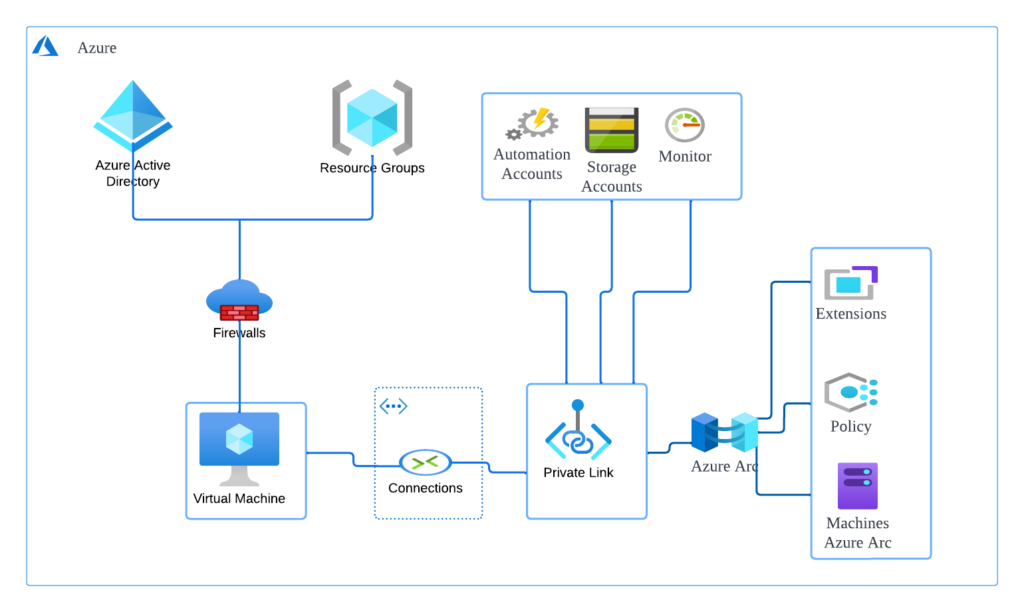
Starting with servers that support Azure Arc, you may utilize a Private Link Scope model to enable numerous servers or computers to connect to their Azure Arc resources through a single private endpoint.
There are advantages
- No public network access is required to connect to Azure Arc privately.
- Make sure that only permitted private networks are used to access data from the Azure Arc-enabled machine or server. This also contains information from any installed VM extensions that provide post-deployment management and monitoring.
- By designating particular Azure Arc-enabled servers and other Azure services resources, like Azure Monitor, that connect through your private endpoint, you may prevent data exfiltration from your private networks.
- Utilize ExpressRoute and own Link to safely link your own on-premises network to Azure Arc.
- Keep all traffic within the backbone network of Microsoft Azure.
Restrictions and limitations
The Azure Arc-enabled servers Private Link Scope object has a number of limits you should consider when planning your Private Link setup.
- You can associate at most one Azure Arc Private Link Scope with a virtual network.
- An Azure Arc-enabled machine or server resource can only connect to one Azure Arc-enabled servers Private Link Scope.
- All on-premises machines need to use the same private endpoint by resolving the correct private endpoint information (FQDN record name and private IP address) using the same DNS forwarder. For more information, see Azure Private Endpoint DNS configuration
- The Azure Arc-enabled server and Azure Arc Private Link Scope must be in the same Azure region. The Private Endpoint and the virtual network must also be in the same Azure region, but this region can be different from that of your Azure Arc Private Link Scope and Arc-enabled server.
- Network traffic to Azure Active Directory and Azure Resource Manager does not traverse the Azure Arc Private Link Scope and will continue to use your default network route to the internet. You can optionally configure a resource management private link to send Azure Resource Manager traffic to a private endpoint.
- Other Azure services that you will use, for example Azure Monitor, requires their own private endpoints in your virtual network.
- Remote access to the server using Windows Admin Center or SSH is not supported over private link at this time.
Preparing to set up a private link
You must set up your network so that it can do the following tasks in order to connect your server to Azure Arc over a private link:
1. Establish a connection between your on-premises network and an Azure virtual network using a site-to-site VPN or ExpressRoute circuit.
2. Create an Azure Arc Private Link Scope and connect it to your Azure virtual network via a private endpoint. This scope regulates which computers or servers can communicate with Azure Arc over private endpoints.
3. Change your local network’s DNS setup to resolve the private endpoint addresses.
4. Set up your local firewall to permit access to Azure Resource Manager and Azure Active Directory.
5. Assign the private link scope to the devices or servers registered with Azure Arc-enabled servers.
6. Deploy private endpoints if desired for the additional Azure services your machine or server uses, such as:
Azure Monitoring and Automation
Blob storage in Azure
Azure Key Vault
Refer- Securely link servers to Azure Arc using Azure Private Link