Hi IT Pro,
The following is step-by-step document for Defender for Endpoint Linux (MD ATP for Linux) deployment.
Let’s start your MD for Endpoint Linux deployment!
________________________________
Microsoft Defender for Endpoint Linux (MD ATP)support for Linux with kernel version 3.10.0-327 or later, including the following Linux flavours :
- Red Hat Enterprise Linux 7.2 or higher
- CentOS 7.2 or higher
- Ubuntu 16.04 LTS or higher LTS
- Debian 9 or higher
- SUSE Linux Enterprise Server 12 or higher
- Oracle Linux 7.2 or higher
MD ATP provide real-time protection for the following file system types:
| btrfs | ecryptfs | ext2 |
| ext3 | ext4 | fuse |
| fuseblk | jfs | nfs |
| overlay | ramfs | reiserfs |
| tmpfs | udf | vfat |
| xfs |
Deployment MD for Endpoint prerequisite:
- Administrative privileges on the device (in case of manual deployment)
- The fanotify kernel option must be enabled,
- For RedHat Enterprise Linux 7.x and CentOS 7.x systems, the kernel module is enabled by default.
- For Ubuntu, SUSE, and Oracle Enterprise Limited, Fanotify is enabled by default.
- Disk space: 650 MB
- No other fanotify-based security solutions running on same Linux Computer.
- Network connections
- Set firewall outbound connection rules to allow these URLs.
| Service location | DNS record |
| Common URLs for all locations | x.cp.wd.microsoft.com cdn.x.cp.wd.microsoft.com eu-cdn.x.cp.wd.microsoft.com wu-cdn.x.cp.wd.microsoft.com officecdn-microsoft-com.akamaized.net crl.microsoft.com events.data.microsoft.com |
| European Union | europe.x.cp.wd.microsoft.com eu-v20.events.data.microsoft.com usseu1northprod.blob.core.windows.net usseu1westprod.blob.core.windows.net |
| United Kingdom | unitedkingdom.x.cp.wd.microsoft.com uk-v20.events.data.microsoft.com ussuk1southprod.blob.core.windows.net ussuk1westprod.blob.core.windows.net |
| United States | unitedstates.x.cp.wd.microsoft.com us-v20.events.data.microsoft.com ussus1eastprod.blob.core.windows.net ussus1westprod.blob.core.windows.net |
- If a proxy or firewall is blocking anonymous traffic, make sure that anonymous traffic is permitted in the previously listed URLs.
- For transparent proxies, no additional configuration is needed
- For static proxy, follow the steps in Manual Static Proxy Configuration.
DEPLOYMENT OPTIONS
MD for Endpoint deployment go through 4 steps as follow:
- Configure the Linux software repository (Linux download channel)
- Application installation
- Download the onboarding package
- Client configuration (Onboarding Linux Client)
MANUAL DEPLOYMENT (using YUM Utility)
- Install Yum Utility for package installing and uninstalling
- If the Server is RHEL and newly build, you have to register it with Redhat first.
- It may take more than 30 minutes for all the RHEL download and Linux update packages.
- Yum update && yum install yum-utils
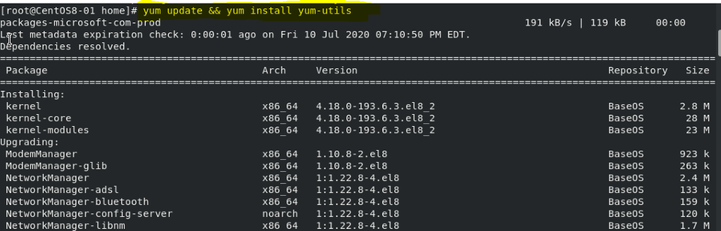
- Microsoft Defender for Linux can be deployed from one of the following channels (denoted below as [channel]🙁 insiders-fast, insiders-slow, or prod. Each of these channels corresponds to a Linux software repository
- RHEL and variants (CentOS and Oracle Linux)
sudo yum-config-manager --add-repo=https://packages.microsoft.com/config/[distro]/[version]/[channel].repo
If you want to check current Linux distro and version, run the command:
cat/etc/os-release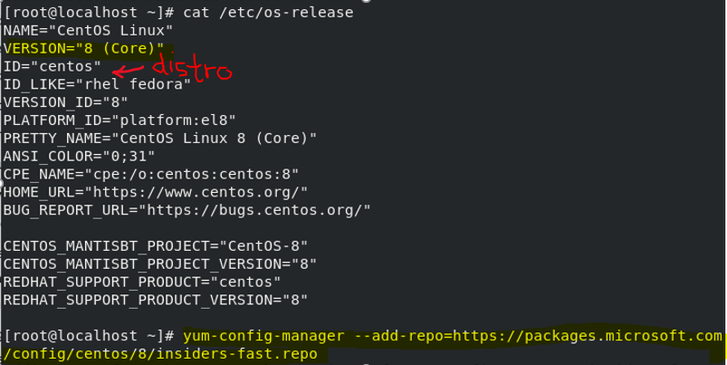
- Install the Microsoft GPG public key:
sudo rpm --import http://packages.microsoft.com/keys/microsoft.asc- Download and make usable all the metadata for the currently enabled yum repositories:
yum makecache- RHEL and variants (CentOS and Oracle Linux):
sudo yum install mdatp
Downloading the Onboarding package from MD ATP Portal
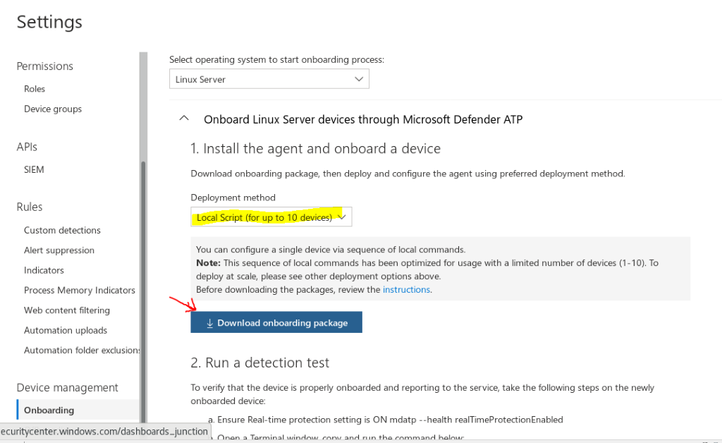
Download the onboarding package from Microsoft Defender Security Center:
- In Microsoft Defender Security Center, go to Settings > Device Management > Onboarding.
- In the first drop-down menu, select Linux Server as the operating system. In the second drop-down menu, select Local Script (for up to 10 devices) as the deployment method.
- Select Download onboarding package. Save the file as WindowsDefenderATPOnboardingPackage.zip.
Client Configuration (Onboarding Linux Client)
- Make sure Python3 is in system ‘s path
sudo alternatives --set python /usr/bin/python- Copy MicrosoftDefenderATPOnboardingLinuxServer.py to the target device
- On the target device
python MicrosoftDefenderATPOnboardingLinuxServer.py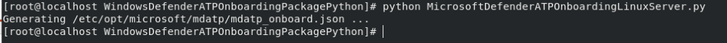
- Verify that the device is now associated with your organization
mdatp health --field org_id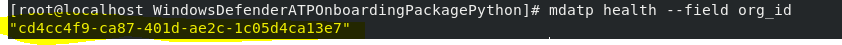
- Verify that the device is properly onboarded and reporting to the service
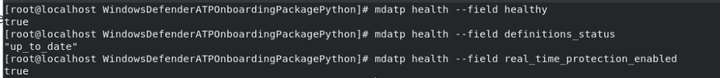
Monitoring new Linux Client on ATP Portal
- Check if Linux Machine is display in ATP Portal Dashboard

How to configure Microsoft Defender for Endpoint on Linux Server
Location of mdatp configuration file: /etc/opt/microsoft/mdatp/managed/mdatp_managed.json
- In enterprise environments, Microsoft Defender ATP for Linux can be managed through a configuration profile
- The configuration profile is a .json file that consists of entries identified by a key (which denotes the name of the preference), followed by a value.Values can be simple, such as a numerical value, or complex, such as a nested list of preferences.
- Typically, you would use a configuration management tool to push a file with the name mdatp_managed.json at the location /etc/opt/microsoft/mdatp/managed/.
mdatp_managed.json preference key and value
| KEY | VALUE | |
| Enable / disable real-time protection | enableRealTimeProtection | true (default)/false |
| Enable / disable passive mode(In passive mode:• Real-time protection is turned off.• On-demand scanning is turned on.• Automatic threat remediation is turned off.• Security intelligence updates are turned on.• Status menu icon is hidden. | passiveMode | true/false (default) |
| Scan exclusions | exclusions | $typeexcludedPath excludedFileExtension excludedFileName |
| Path to excluded content | path | valid paths (string) |
| Enable/Disable Delivered Cloud Protection | enabled | true (default)/false |
Recommended configuration profile
To get started, we recommend the following configuration profile for your enterprise to take advantage of all protection features that Microsoft Defender for Endpoint Linux provides.
The following configuration profile will:
- Enable real-time protection (RTP)
- Specify how the following threat types are handled:
- Potentially unwanted applications (PUA) are blocked
- Archive bombs (file with a high compression rate) are audited to the product logs
- Enable automatic security intelligence updates
- Enable cloud-delivered protection
- Enable automatic sample submission at safe level
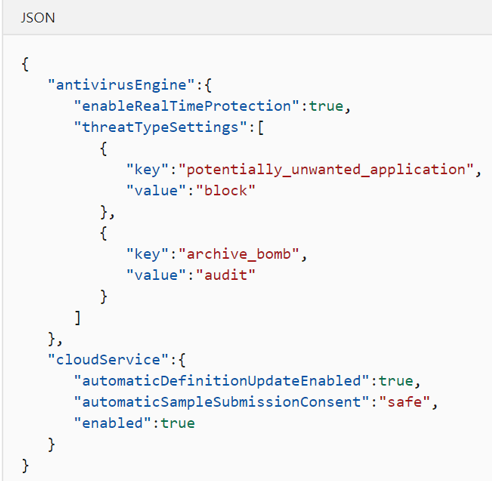
More MD for Endpoint Preference Configuration
Configuration profile deployment by Linux Management:
Once you’ve built the configuration profile for your enterprise, you can deploy it through the management tool that your enterprise is using. Microsoft Defender ATP for Linux reads the managed configuration from the /etc/opt/microsoft/mdatp/managed/mdatp_managed.json file.
Update Microsoft Defender for Endpoint on Linux server
Each version of Microsoft Defender ATP for Linux has an expiration date, after which it will no longer continue to protect your device.
To check the MD for Endpoint expiration date, run the following bash command:
mdatp health --field product_expirationTo update Microsoft Defender for Endpoint on Linux manually, execute one of the following commands:
RHEL and variants (CentOS and Oracle Linux)
sudo yum update mdatpSLES and variants
sudo zypper update mdatpUbuntu and Debian systems
sudo apt-get install --only-upgrade mdatpTROUBLESHOOTING
Troubleshoot installation issues:
To verify if the installation succeeded, one can obtain installation.log and search the installation logs for “postinstall end” phrase, using these commands:
sudo journalctl | grep 'microsoft-mdatp' > installation.loggrep 'postinstall end' installation.log
Troubleshooting Connectivity:
Run the connectivity test
mdatp connectivity test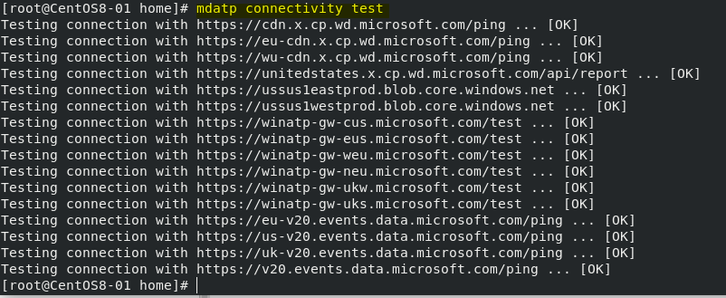
Troubleshooting Performance:
To find the applications that are triggering the most scans, you can use real-time statistics gathered by Microsoft Defender for Endpoint on Linux.
mdatp diagnostic real_time_protection_statistics > stat.logThis feature is enabled by default on the Dogfood and InsisderFast channels. If you’re using a different update channel, this feature can be enabled from the command line:
mdatp config real-time-protection-statistics --value enabledMore Troubleshooting:
Installation
Performance
Network Connectivity
I hope the information is useful to you. Please provide feedback.