There are various instances where you would need to use credentials, tokens, API keys etc. to access certain services. For example, you would need to use your SQL server credentials to access certain DB for your application. But, storing those in the codebase as a plain text file is not the best idea. It is a security vulnerability. Anyone with access to your codebase would be able to read those secrets and get unauthorized access to your services and perform malicious actions. You could encrypt the secrets, and share the key external to your application as a config file to allow for decryption.
AWS Secrets Manager
This service allows you to protect secrets needed to access your applications, services and IT resources. One can easily rotate, manage, and retrieve database credentials, API keys, and other secrets throughout their lifecycle. Users and applications retrieve secrets with a call to Secrets Manager APIs, eliminating the need to hardcode sensitive information in plain text. The service is extensible to other types of secrets, including API keys and OAuth tokens. Moreover, you can control access to secrets using fine-grained permissions and audit secret rotation centrally for resources in the AWS Cloud, third-party services, and on-premises. The secrets can be replicated to other regions easily to support multi-region applications. Now we will look at the steps required to create a secret and retrieve it programmatically.
Step 1: Creating and storing the secret
You can use the AWS Secrets manager console or the AWS CLI for creating the secrets.
Secrets Manager Console
- Sign in to the console at: https://console.aws.amazon.com/secretsmanager/
2. On the Secrets list page click on Store a new secret.

3. On the Store a new secret page, select Other type of secret. (This type allows you to store key value pairs or plain text.) You can then specify the secrets as key value pairs on this page. Your key could for example be “username” and value “secmanager@aws.com”
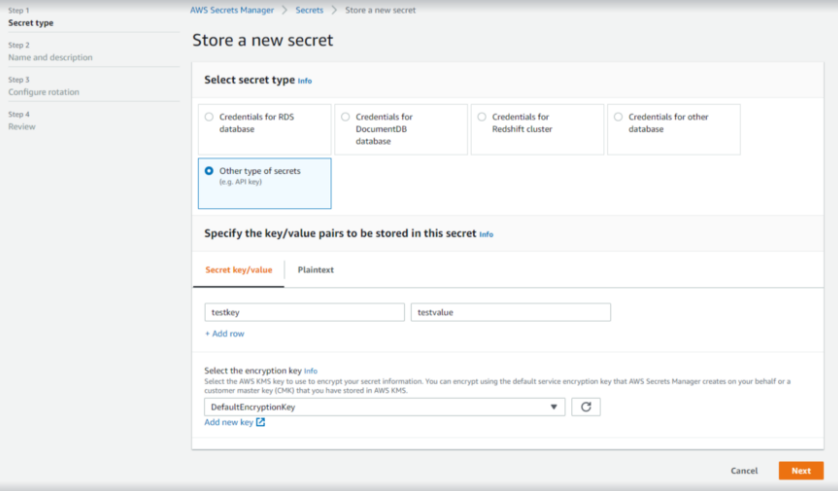
4. For Select the encryption key, choose DefaultEncryptionKey. Secrets Manager always encrypts the secret when you select this option at no extra cost.
5. Choose Next
6. Under Secret name, type a name for the secret. It can be only alphanumeric and /_+=.@-. The example you can use: tutorial/firstkey. The hierarchy allows you to group your secrets and maintain them better. You can add a description, tags, here if you want.
7. Press Next.
8. Review the final details. Also, this page gives you very nice Sample codes for different languages that you can use directly in your application. You can get Python, Java, JavaV2, JavaScript, C#, Ruby and Go language snippets. Pretty neat! Press Store. And this creates a secret called tutorial/firstkey with testkey:testvalue pair as the secret in it.