You may gather Syslog events from Linux nodes in your Azure Kubernetes Service (AKS) clusters using Container Insights. One feature of this is the ability to gather logs from components of the control plane, such as Kubelet.
Prerequisites
- You need to have managed identity authentication enabled on your cluster. To enable, see migrate your AKS cluster to managed identity authentication. Note: Enabling Managed Identity will create a new Data Collection Rule (DCR) named
MSCI-<WorkspaceRegion>-<ClusterName> - Port 28330 should be available on the host node.
- Minimum versions of Azure components
- Azure CLI: Minimum version required for Azure CLI is 2.45.0 (link to release notes). See How to update the Azure CLI for upgrade instructions.
- Azure CLI AKS-Preview Extension: Minimum version required for AKS-Preview Azure CLI extension is 0.5.125 (link to release notes). See How to update extensions for upgrade guidance.
- Linux image version: Minimum version for AKS node linux image is 2022.11.01. See Upgrade Azure Kubernetes Service (AKS) node images for upgrade help.
How to make Syslog active
Using the Azure website– Locate your cluster by navigating. Select your cluster’s Insights tab. Slide open the Monitor Settings menu. To enable Syslog collection, click Edit collection options and check the box.
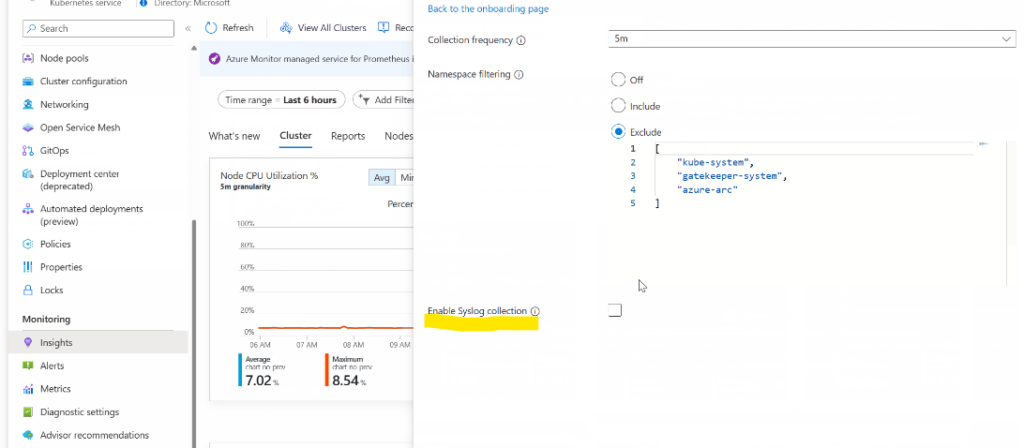
How to get Syslog information
Access using log queries– The Syslog table in your Log Analytics workspace contains the Syslog data. You can create your own log queries in Log Analytics to analyze this data or use any of the prebuilt queries.
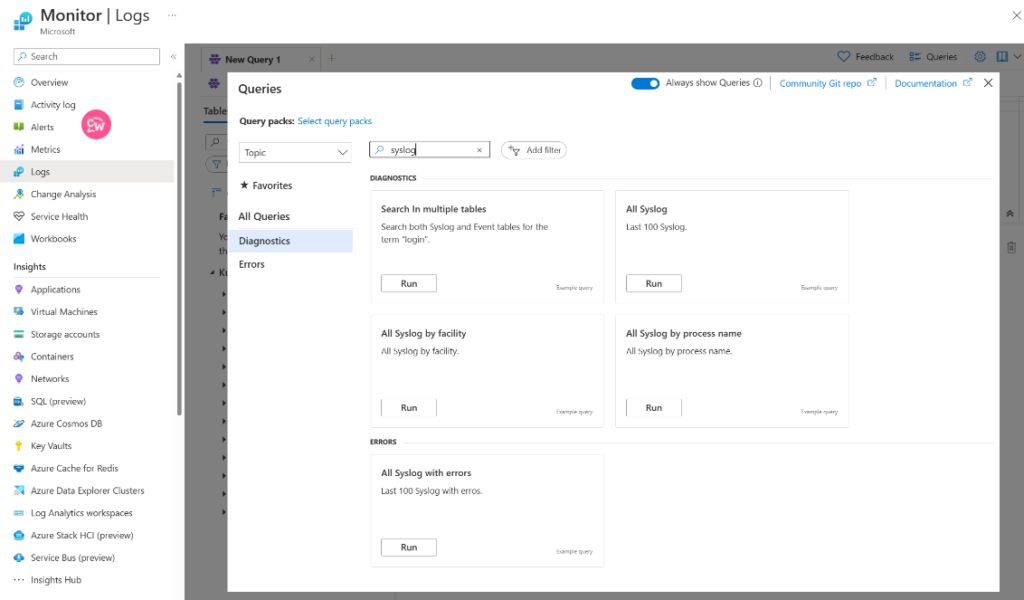
You can open Log Analytics from the Logs menu in the Monitor menu to access Syslog data for all clusters or from the AKs cluster’s menu to access Syslog data for only that cluster.
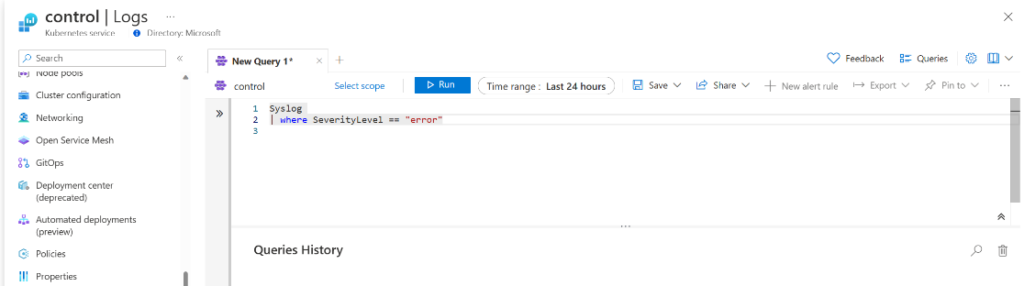
Examples of queries
Several examples of log queries that obtain Syslog records are shown in the following table.
| Query | Description |
|---|---|
Syslog | All Syslogs |
Syslog | where SeverityLevel == "error" | All Syslog records with severity of error |
Syslog | summarize AggregatedValue = count() by Computer | Count of Syslog records by computer |
Syslog | summarize AggregatedValue = count() by Facility | Count of Syslog records by facility |
Syslog | where ProcessName == "kubelet" | All Syslog records from the kubelet process |
Syslog | where ProcessName == "kubelet" and SeverityLevel == "error" | Syslog records from kubelet process with errors |
Changing the Syslog collection configuration – You can change the data collection rule (DCR) that was generated when you activated Syslog collection to change the configuration for your Syslog collection.
From the Azure portal, choose Data Collection Rules by clicking on the Monitor menu.
After choosing your DCR, Examine the data sources. To view the specifics of the Syslog collection, select the Linux Syslog data source.
Refer- Container Insights to collect Syslog events from Linux nodes in AKS clusters.